Blocking Windows Recall Enabled Managed Devices
Whether we like it or not, AI and Copilot is everywhere, and even if you don't want AI backed features like Windows Recall enabled on managed corporate and BYOD devices, it will happen. So how do we block these Copilot+ devices from accessing Corporate data or services?
I’m not a fan of scaremongery when it comes to privacy and AI functionality, especially Microsoft Copilot AI features; but I am aware that even with all the configuration options you have at your fingertips with Intune to limit what AI features for Windows Recall can be used on managed devices, there is still a security concern with data that is captured and stored, or even accessed.
So what do we do about the Windows Recall functionality that can record your screen, on both corporate owned and BYOD devices.
Disable Windows Recall
Well Windows Recall is disabled and removed on commerical devices by default at least, but let’s just make sure and enforce this disablement using Intune, and push out this new Settings Catalog policy to all supported (10.0.26100.3915 and above) devices, because you know, fear 👻.
| Category | Setting | Value |
|---|---|---|
| Windows AI | Allow Recall Enablement | Recall is not available |
| Windows AI | Allow Recall Export | Deny export of Recall and snapshots information |
| Windows AI | Disable AI Data Analysis | Disable Saving Snapshots for Windows. |
What if, just what if, someone with Administrator permissions goes and changes these settings manually or enables the Windows Optional Feature. What do we do then?
Device Compliance
We mark them as non-compliant and block then with a Conditional Access policy. Next.
Ok, we should expand on this a little bit, Custom Compliance allows additional checks on Windows (and Linux) devices, that native compliance checks don’t support.
Essentially, if you can script something self-contained (i.e., it isn’t calling external web services or apis for information) that will run on the device in the SYSTEM or User context to pull back information from the device, you can use that to determine whether a device is going to be marked as compliant or non-compliant.
We’ve used Custom Compliance with Third-Party Antivirus products previously, so let’s look at what we need to detect to understand whether someone on a corporate device has somehow enabled Windows Recall, or someone using BYOD device already has enabled it on their Copilot+ PC.
Device Platform Restrictions
“Oh but Custom Compliance only works on Windows Pro and above, what about Windows Recall running on Windows Home?”, I hear you whinge.
Yeah, you’re not wrong, Custom Compliance is only supported on Windows excluding Windows Home, and Windows Recall has vague enough pre-requisites to make you think it shouldn’t support Windows Home, but in fact it does, kind of.
Have you thought about abusing Device Platform Restrictions and Assignment Filters to block the enrolment of Windows Home devices though?
Easy enough to implement, but a bigger question on whether you would want to, either way I want to as it’s not like you can really manage Windows Home devices anyway 😂.
Go create a new Windows Assignment Filter with the below rule, which will basically includes all non-home editions of Windows.
(device.operatingSystemSKU -notIn ["Core", "CoreCountrySpecific", "CoreN", "CoreSingleLanguage"])Or for the lazy…
(device.operatingSystemSKU -notContains "Core")Then go amend your Device Platform Restriction policy that allows Windows BYOD, and apply the new filter.
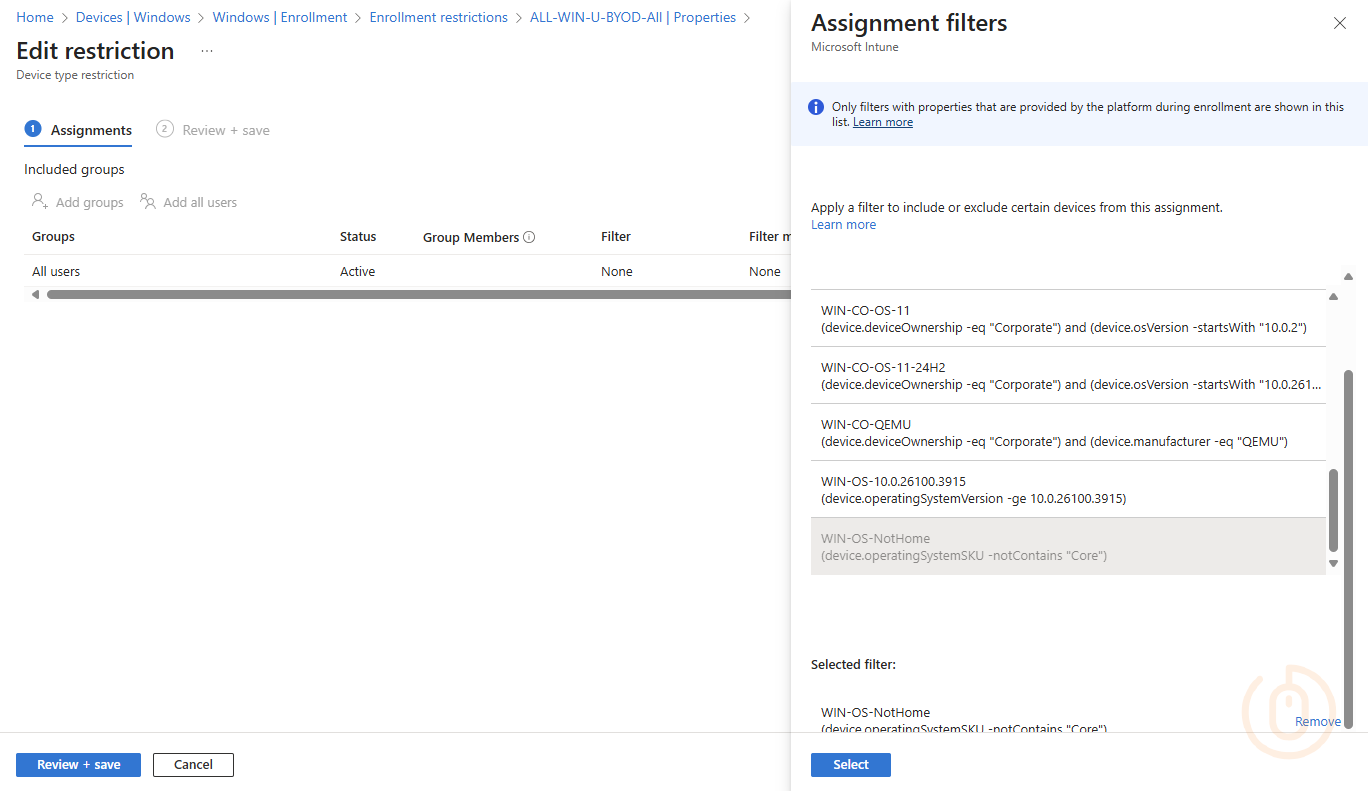
Now with BYOD Windows Home editions blocked from enrolment, and therefore unable to be marked as compliant, we can sleep safe at night (well after you remove all existing Windows Home BYOD devices from Intune 😶).
There isn’t the option to use an exclude mode for the Filter in the web interface at least, hence the use of notIn in the filter.
Also, ensure that the default All users Platform Restriction is blocking Personally owned enrolment for Windows devices.
Detection Methods
Back to Windows Recall and compliance.
Short of confirming whether the Windows Recall settings we pushed to devices using Intune have applied correctly, what else do we need to check on the device to be sure Windows Recall isn’t snooping and listening working in the background?
Three things really, and all can be used in a Custom Compliance policy to understand whether any or all or the Windows Recall settings are enabled depending on your approach:
- Whether the Windows Recall Feature itself is installed
- Whether the corresponding registry setting for Allow Recall Enablement has been set
- Whether the corresponding registry setting for Disable AI Data Analysis has been set
Pretty straightforward really, just a bit of PowerShell to work out whether the feature is installed and whether the registry settings exist and are set to the correct values.
Windows Recall Feature
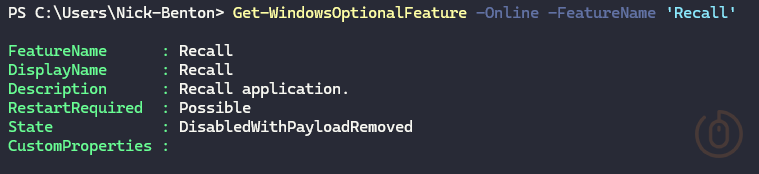
We can work out whether the feature itself is installed using a simple one-liner.
Get-WindowsOptionalFeature -Online -FeatureName 'Recall'With the results of the above allowing us to query the state property as to whether Recall is installed or not.
Windows Recall Registry Entries
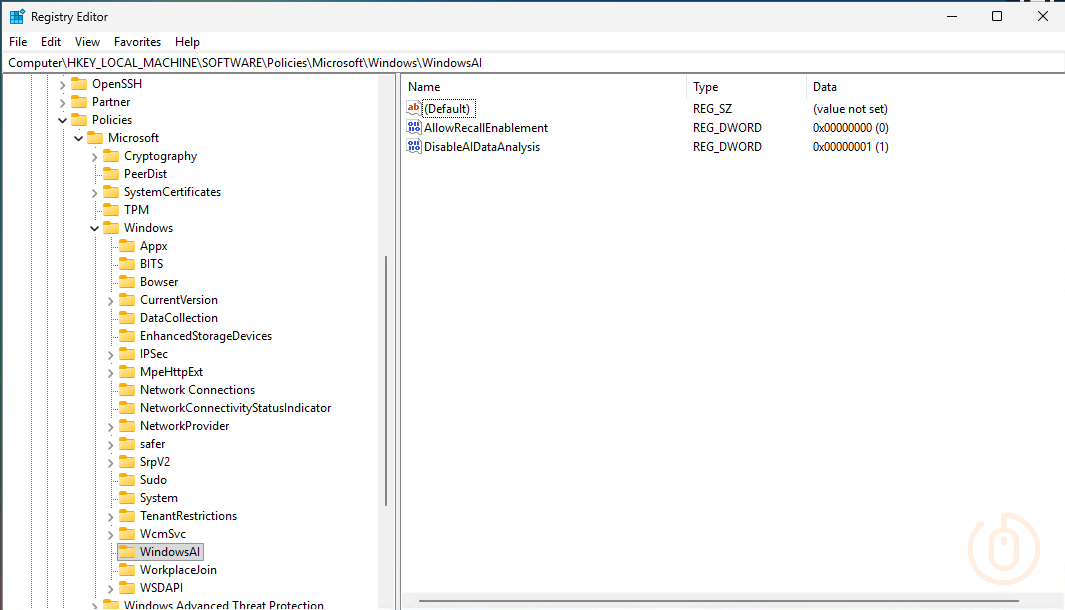
Both ‘Allow Recall Enablement’ and ‘Disable AI Data Analysis’ registry settings exist in the same key in the registry HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsAI, meaning that we can just query the below two settings and their values to ensure that Windows Recall is disabled.
AllowRecallEnablementequal to0DisableAIDataAnalysisequal to1
I am aware that DisableAIDataAnalysis also exists in the Current User Registry Hive, but if we’re going to use Custom Compliance on BYOD as well as corporate owned Windows devices, we might struggle getting user context scripts to work due to certain limitations.
Plus we’re still detecting if the Windows Recall feature is installed, so do one, get off my back there we go 😅.
Custom Compliance
Now we know what can be queried to understand whether Windows Recall is enabled on a device or not, we can create a discovery script with these detection methods to be used for a Custom Compliance policy.
Discovery Script
The below script discovers whether the Windows Recall feature is installed, and the registry keys exist, and are set to the correct values, and presents back a JSON object that Intune can use for validation.
$complianceSummary = New-Object -TypeName PSObject
$featureRecall = (Get-WindowsOptionalFeature -Online -FeatureName 'Recall')
if ($featureRecall.State -eq 'Enabled') {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall Feature' -Value 'Enabled'
}
else {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall Feature' -Value 'Disabled'
}
if ((Get-Item 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsAI\' -ErrorAction Ignore).Property -contains 'AllowRecallEnablement') {
if ((Get-ItemPropertyValue -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsAI\' -Name 'AllowRecallEnablement') -eq 0) {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall AllowRecallEnablement' -Value 'Disabled'
}
else {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall AllowRecallEnablement' -Value 'Enabled'
}
}
else {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall AllowRecallEnablement' -Value 'Enabled'
}
if ((Get-Item 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsAI\' -ErrorAction Ignore).Property -contains 'DisableAIDataAnalysis') {
if ((Get-ItemPropertyValue -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsAI\' -Name 'DisableAIDataAnalysis') -eq 1) {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall DisableAIDataAnalysis' -Value 'Enabled'
}
else {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall DisableAIDataAnalysis' -Value 'Disabled'
}
}
else {
$complianceSummary | Add-Member -MemberType NoteProperty -Name 'Windows Recall DisableAIDataAnalysis' -Value 'Disabled'
}
return $complianceSummary | ConvertTo-Json -CompressWhich when testing from an elevated PowerShell prompt should give us a happy outcome.
{"Windows Recall Feature":"Disabled","Windows Recall AllowRecallEnablement":"Disabled","Windows Recall DisableAIDataAnalysis":"Enabled"}JSON Validation
With a discovery script, we also need a corresponding JSON file to ensure that we can check the data captured by the discovery script against our benchmark for device compliance.
{
"Rules": [
{
"SettingName": "Windows Recall Feature",
"Operator": "IsEquals",
"DataType": "String",
"Operand": "Disabled",
"MoreInfoUrl": "https://learn.microsoft.com/en-us/windows/client-management/manage-recall",
"RemediationStrings": [
{
"Language": "en_US",
"Title": "Windows Recall",
"Description": "The Windows Recall Feature must be disabled on your computer to be marked as compliant."
}
]
},
{
"SettingName": "Windows Recall AllowRecallEnablement",
"Operator": "IsEquals",
"DataType": "String",
"Operand": "Disabled",
"MoreInfoUrl": "https://learn.microsoft.com/en-us/windows/client-management/manage-recall#allow-recall-and-snapshots-policies",
"RemediationStrings": [
{
"Language": "en_US",
"Title": "Windows Recall",
"Description": "The value for 'AllowRecallEnablement' under registry key 'HKLM:\\SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsAI' must be set to 0 (Disabled) on your computer to be marked as compliant."
}
]
},
{
"SettingName": "Windows Recall DisableAIDataAnalysis",
"Operator": "IsEquals",
"DataType": "String",
"Operand": "Enabled",
"MoreInfoUrl": "https://learn.microsoft.com/en-us/windows/client-management/manage-recall#allow-recall-and-snapshots-policies",
"RemediationStrings": [
{
"Language": "en_US",
"Title": "Windows Recall",
"Description": "The value for 'DisableAIDataAnalysis' under registry key 'HKLM:\\SOFTWARE\\Policies\\Microsoft\\Windows\\WindowsAI' must be set to 1 (Enabled) on your computer to be marked as compliant."
}
]
}
]
}This JSON file not only allows for validation of the settings, but also what information is displayed to the end users in the Company Portal when their device is marked as non-compliant, friendly 😇.
Compliance Policy
With all we need at our disposal, head into Intune and navigate to Devices > Manage Devices > Compliance > Scripts and add our discovery script for Windows 10 and later devices.
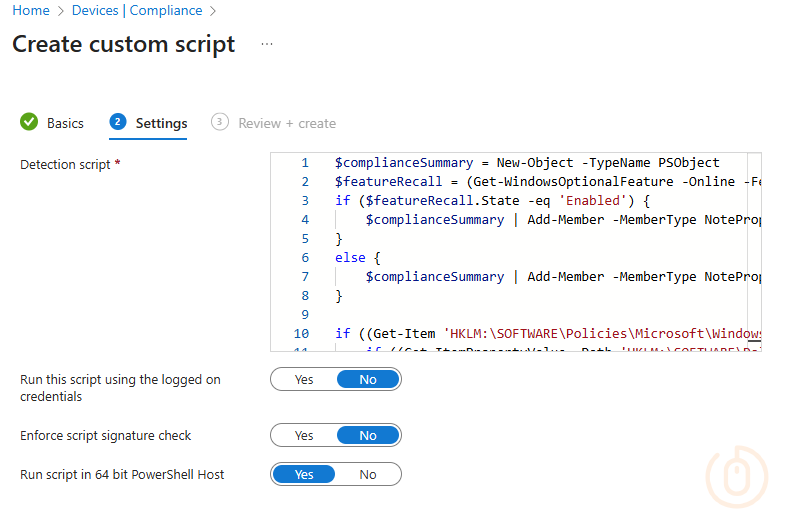
Now just to create the Compliance Policy to use the script we created, and upload the JSON file for validation.
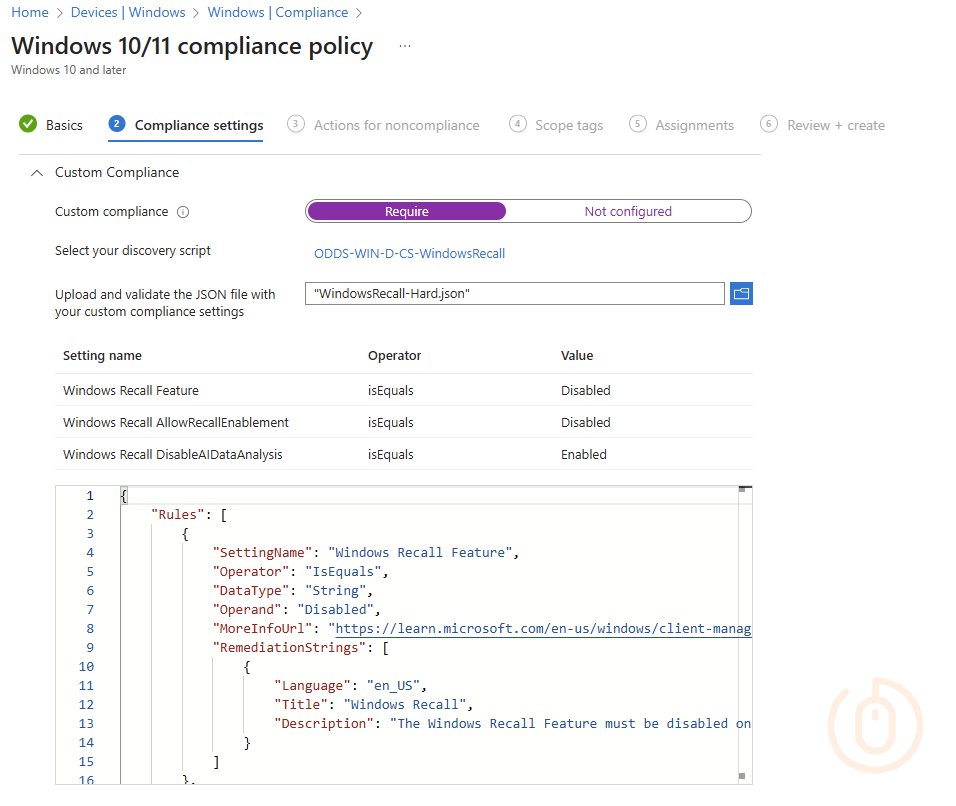
All is left is to deploy the script to your chosen groups of devices, for me this is all of them running a supported version of Windows (10.0.26100.3915 and above), and sit back and wait for the results to come in…
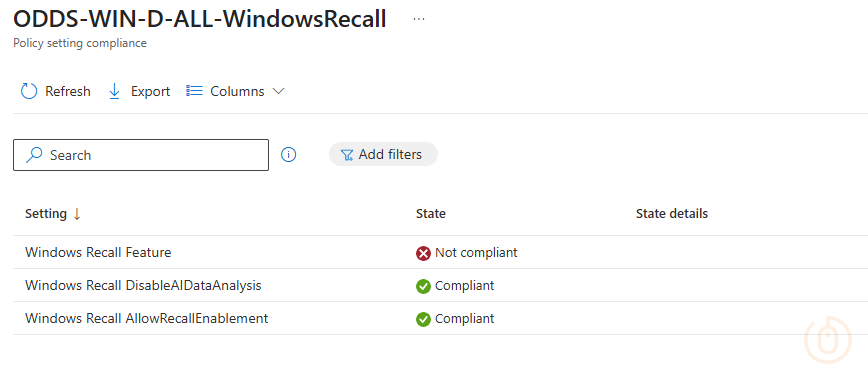
(device.operatingSystemVersion -ge 10.0.26100.3915) if you like.With the polite notice configured in the JSON file, users at least get told in the Company Portal why they’re being marked as non-compliant, with a nice link telling them how to fix it.
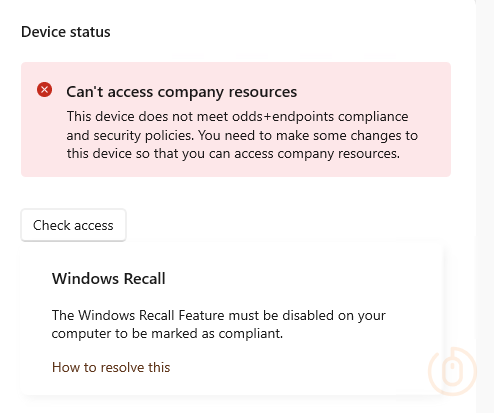
Once we’re happy that the compliance policy is applying as expected and marking devices as non-compliant where Windows Recall is enabled, you can blindly create a Conditional Access Policy to require Device Compliance, blocking devices that are non-compliant, now including those with Windows Recall or associated settings enabled.
Summary
We should be embracing AI even if it will come for all our jobs at some point, or at least write blog posts about Intune for us 👀.
For now though we should be combatting our AI overlords conscious of the use of AI functionality on corporate owned devices, or devices accessing corporate data held in Microsoft services, and putting in place suitable controls to manage or mitigate the use of things like Windows Recall.
Luckily for you, me and my mate Microsoft have the functionality to both limit the use of Windows Recall or just full on block devices where Windows Recall is enabled.
Shout out to Petr Pospíšil whose LinkedIn post got me annoyed enough to write this blog post 😘.